Navigating Endpoint Management: Your Complete Handbook
With remote work becoming the new normal and advanced technologies changing industries’ landscape, technicians are struggling to protect a larger fleet of devices and fend off cyber-attacks. As a result, the need for endpoint management tools has become more pressing.
Which is why we will talk more endpoint management features, why it is important for your business, and share some of the recommended software with you. Read on for more details!
- Part 1 :What is Endpoint Device Management?
- Part 2 :What Kind of Endpoint Devices Do We Need to Manage?
- Part 3 :The Difference between EMM, MDM, UEM
- Part 4 :Why is Endpoint Management Important to Your Business?
- Part 5 :Key Functions of An Endpoint Management Software
- Part 6 :Unified Endpoint Management Use Cases
- Part 7 :Best Endpoint Management Software for Business

- Part 8 :The Role of Endpoint Device Management in the Modern Business Environment
- Part 9 :Conclusion
- Part 10 :FAQs
Part 1. What is Endpoint Device Management?
Endpoint management is the process of actively monitoring, detecting, and preventing malware attacks on devices that are connected to a network.
This is typically done using a unified endpoint management (UEM) platform, which allows IT staff to implement security policies and monitor suspicious activities on endpoints.

Part 2. What Kind of Endpoint Devices Do We Need to Manage?
Some common examples of endpoints include desktop computers, printers, laptops, on-premise servers, smartphones, tablets, IoT devices, Point of Sale (POS) systems, switches, and any other network-enabled devices. These endpoints are usually targeted by cyberattacks, and making their proper management crucial to network security.
For instance, RSA Security found that more than 60% of fraud originates from mobile devices.
Endpoint devices need to be managed because they are often the entry points for cyber-attacks on an organization's network. Endpoints can be vulnerable to malware, viruses, and other types of cyber threats, which can compromise the security and privacy of the organization's data.
Endpoint management helps ensure that endpoints are secure and compliant with regulations and standards by enforcing security policies, monitoring for vulnerabilities, and performing routine maintenance tasks such as patching and software updates.
Ultimately, managing and securing endpoint devices will block almost all the entry points hackers can use to access and organization’s network and other IT resources.

Part 3. The Difference between EMM, MDM, UEM
EMM, MDM, and UEM and the three different types of endpoint management. Let’s explain each of these in detail;
Mobile Device Management (MDM)
MDM is a type of endpoint management solution designed to manage and secure mobile devices, such as smartphones and tablets issued by an organization, Point of Sale (POS) devices, single-app mode devices, which don’t involve Bring Your Own Device (BYOD).
MDM solutions provide essential features, including device enrollment, configuration management, software distribution, and enforcement of security policies. These features play a crucial role in ensuring the secure and efficient management of mobile devices.
Enterprise Mobility Management (EMM)
EMM is a type of endpoint management solution that focuses on managing and securing mobile devices and applications. These usually involve smartphones and tablets running Android, iOS, or iPadOS operating Systems.
Besides the devices issued by an organization, EMM solution also allows employees to enroll their own devices into the organization’s IT resources. The core components of EMM solutions include mobile device management (MDM), mobile application management (MAM), mobile content management (MCM), and mobile identity management (MIM).
Unified Endpoint Management (UEM)
UEM is an endpoint management solution that focuses on managing and securing all types of endpoints, including mobile devices, IoT devices, desktops, laptops, and servers. UEM is the most sophisticated type of endpoint management solution since it requires managing and securing different kinds of devices across a network.
The core components of UEM solutions include device enrollment, device configuration management, software distribution, security policy enforcement, and endpoint analytics.
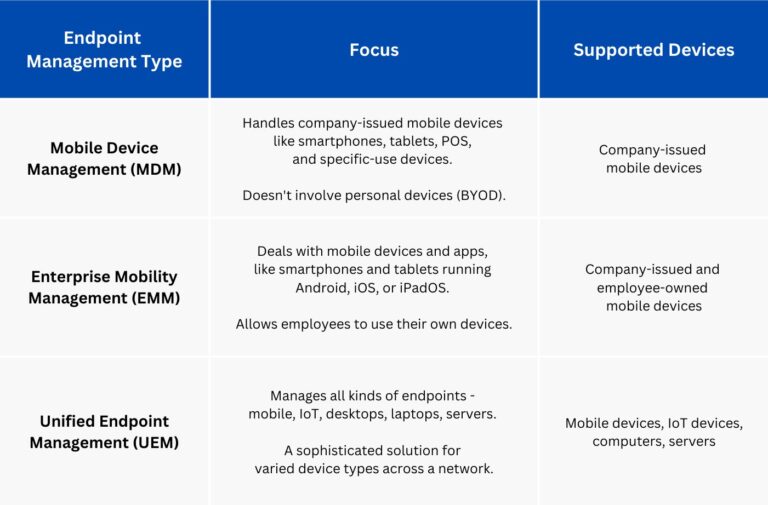
Overall, the main difference between these three types of endpoint management solutions - MDM, EMM, and UEM - is the scope of devices and applications they manage.
MDM focuses on managing and securing mobile devices, EMM expands to manage mobile applications, and UEM covers all types of endpoints.
By leveraging UEM solutions, organizations can effectively manage and secure their endpoints, streamline IT operations, and improve efficiency.
Part 4. Why is Endpoint Management Important to Your Business?
Endpoint security has risen to be one of the top concerns for businesses globally as they explore ways to ensure the security of their data and tech infrastructure. Some of the reasons why it is important for your business include the following.
1. Rising Cases of Cybersecurity Attacks
In 2019, the FBI, in its Internet Crime Report, revealed that reported cybercrime complaints surpassed 300,000 and cost more than $4.2 billion. Fast forward to 2021, the report indicates at least 847,376 complaints costing $6.9 billion or more. These numbers point to an upward trend in cybersecurity attacks, signaling the need for businesses to have an endpoint management strategy in place to ensure that they can fend off consistent threats.

2. More Flexibility on Employee-Owned Devices
We are in the age of remote and hybrid work, and more businesses will continue to shift to this working model. According to Technavio’s report, the global bring your own device (BYOD) market is expected to increase in size by USD 69.07 from 2021 to 2026, hence more exposure to threats. Distributed teams mean less control over the endpoints, creating further vulnerabilities that hackers may look to exploit.

3. Increased Device Deployment
In addition to the impact of remote work, businesses are also adopting more devices into their workflows to ensure a better work efficiency and services.
For instance: Healthcare industries have been using wearable devices to monitor patients’ health status, so they can provide timely treatment. Retail businesses also deploy more digital signage, self-service kiosks, and staff work devices to create more convenient and interactive shopping environment, while increasing store productivity.
However, this trend also presents challenges for industries in terms of managing their fleet of devices without significantly increasing IT costs.
Part 5. Key Functions of An Endpoint Management Software
The endpoint management software you choose for your enterprise must comprise certain features that help you stay vigilant and protect your corporate network. The endpoint management software you implement should be able to;
1Remotely Manage and Monitor Endpoint Assets
Endpoint management software gives technicians the flexibility to remotely manage and monitor all the devices on one centralized console, which allows them to provide timely maintenance without going onsite. They can also monitor screen displays, data traffic, device status and health to identify issues and potential risks.
When deploying a new fleet of devices, instead of configuring them one by one, technicians can create a predefined device provisioning template to push secure settings automatically to devices, saving time and effort spent on repetitive work while making sure every device is taken care of.
2Enforce Security Policy on Devices
Security policies are proactive measures that help to prevent data breaches or leaks right from the source.
Technicians can configure dedicated operating environments to ensure that security principles, such as the principle of least privilege and the use of security authentication measures like lock screen passwords and multi-factor authentication (MFA), are followed. Other measures also include application blocklists and data loss prevention policies (DLP).

3Deploy Patches and Ensure Device Compliance
Patch updates help to keep endpoint devices up to date and fix issues that could compromise security. This process is important for addressing vulnerabilities that could be exploited by cyber attacks.
An endpoint management software should also allow you to identify any devices that are not compliant with the latest patch updates.

4Install and Update Applications or Operating Systems on Devices
Outdated operating systems on endpoint assets might be exploitated by malicious hackers to infiltrate a network.
To prevent this, it is important to use an endpoint management software that enables you to automatically update operating systems and applications from a central location, rather than leaving the risk of a security breach open to chance.
5Threat Detection and Remediation
Endpoint management software can alert IT staff to potential issues before they become more serious problems. This feature is often paired with automated workflow capabilities, which can troubleshoot problems on the spot when alerts are triggered.
By addressing issues in this way, IT staff can reduce device downtime more efficiently without the need to send people onsite.
Part 6. Unified Endpoint Management Use Cases
UEM provides a comprehensive solution for managing and securing endpoints across an organization. Here are some common cases of Unified End Point Management and their benefits:
1Mobile device management
UEM provides a unified approach to managing and securing mobile devices such as smartphones, wearables, and tablets. With UEM, IT teams in companies can enroll, configure, and manage mobile devices, apply security policies, distribute apps and updates, and monitor device performance, all from a single console.
For example, in retail scenario, UEM can be used to manage POS devices, ensuring secure payment processing and preventing data breaches.
2PC management
UEM enables IT teams to manage and secure PCs across the organization, regardless of the operating system. With UEM, IT teams can deploy, configure, and manage PCs, enforce security policies, distribute software and updates, and troubleshoot issues, all from a central console.
In education, UEM are usually used in managing classroom devices, ensuring that students have access to the tools and resources they need while also maintaining security and privacy.
3Highly secure and/or regulated industries
In industries such as healthcare, finance, and government, where security and compliance are critical, UEM provides a comprehensive solution for managing and securing endpoints.
It also enables IT teams in these industries to enforce security policies, maintain compliance with regulations such as HIPAA and PCI DSS, monitor endpoints for vulnerabilities, and protect sensitive data.
For instance, UEM is used to manage medical devices and ensure that patient data is protected in hospital or healthcare institutions.
4BYOD management
UEM also enables organizations to manage and secure employee-owned devices that connect to the organization's network. This helps ensure that these devices are secure and compliant with company policies.
A great example is managing consultants’ personal devices while they work on client projects.
5User-centric device management
UEM enables IT teams to manage endpoints based on the user rather than the device. With user-centric device management, IT teams can apply policies and configurations based on the user's role or location.
This method is particularly useful in industries like manufacturing, where devices on the factory floor need to be managed based on the role of the employee using them. With UEM, IT teams can ensure that the right tools and resources are available for each task, boosting productivity and efficiency.
Part 7. Best Endpoint Management Software for Business
Debating which endpoint management software to go for to ensure your business or customer data protection? Check out the following recommendations.
1 AirDroid Business
AirDroid Business empowers businesses, IT professionals, and managed service providers to remotely manage unattended Android devices from a central platform. It is a fast, efficient, and safe mobile device management software that will simplify device access and control to ensure adherence to safety policies and minimize risk and misuse.
Key Features
- Alerts and automated workflows: receive alerts when issues are detected and execute automated workflows to solve them upfront
- Broad compatibility: support a wide range of Android-based endpoints, including phone, tablet, POS, kiosk, digital signage, rugged devices, and custom devices
- Security policies: enforce strong lock screen password, multi-factor authentication, application data loss prevention (DLP) policy to protect data security
- Unassisted and easy remote control: provide powerful remote control features and real-time monitoring on unattended devices without rooting
- Application management services: keep business apps up to date by scheduling rollouts based on device group, device type, location and minimize security risks.
- Kiosk Mode: lock Android devices into single or multi-app mode, whitelist websites, and block unauthorized network access to reduce IT workload on device misuse.
2 ManageEngine
ManageEngine is a cloud-based IT platform that provides solutions to secure business endpoints, improve network security, and deliver convenient IT services. It also offers solutions tailored to specific industries to ensure the security of endpoints.
The goal of ManageEngine is to make IT management easy to monitor endpoints, manage software licensing, and reduce data leakage and theft. This is achieved through an intuitive user interface that simplifies endpoint management and makes it more efficient.
Key Features
- Remote assistance
- Easy customization
- Comprehensive mobile device management
- Vulnerability management
- Data loss prevention
3 Hexnode
Hexnode is an ideal SaaS management service for businesses looking for a pay as you grow type of endpoint management solution. You can also try out the service with a 14-day free trial.
Hexnode will enable your business to implement unified device management solutions covering a host of devices, including Android and iOS phones, Windows and Mac computers, TVs, and more. It features customizable solutions that allow you to free your IT team and set up your enterprise for success.
Key Features
- Kiosk Mode
- App management
- Remote control
- OS update management
- Geofencing
4Atera
Atera is an all-in-one IT platform that avails multiple tools to enhance your endpoint assets management efforts. This cloud-based platform allows you to easily integrate with other tools in your enterprise to ensure efficient security of your data and controlled management of devices on the network.
With Atera, you can automate IT scripting to create more possibilities for your IT team and empower them to do more. Enhance threat monitoring, response, and troubleshooting of issues to offer a seamless customer experience.
Key Features
- Remote access
- Network discovery
- Patch management
- IT script automation
- Remotely monitoring and managing unlimited devices
5NinjaOne Endpoint Management
NinjaOne is known for its integration capabilities, enabling your enterprise and IT team to work in auto mode and stay on top of network threats. The cloud platform prioritizes IT team efficiency and enhances users' productivity.
With NinjaOne, you can free up resources in IT department to focus on strategic tasks by automating workflows easily from its dashboard.
Key Features
- Patch management
- Business data backup
- Software deployment
- Remote access
- IT asset management
6Citrix Endpoint Management
Citrix Endpoint Management is a cloud platform that helps to secure distributed networks by modernizing IT security, providing a VPN alternative, and protecting apps and APIs. Its desktop as a service (DaaS) feature aims to help IT teams manage multiple devices easily and improve the user experience.
Key Features
- Zero trust network access without a VPN
- App delivery and security service
- Web app and API protection
- Behavior analytics
7Microsoft Intune
Microsoft Intune is a popular endpoint management software for enterprises already using the Windows platform to manage their mobile devices.It is especially well-suited for enterprises that allow bring-your-own-device (BYOD) practices due to its ease of integration. Its single sign-on automation feature makes device integration fast and efficient.
Key Features
- Multi-factor authentication
- Integration with Microsoft ecosystem
- Remote monitoring and management
- App management
Part 8. The Role of Endpoint Device Management in the Modern Business Environment
Security and Compliance
By enforcing security policies, monitoring for vulnerabilities, and performing routine maintenance tasks such as patching and software updates, endpoint management helps ensure that endpoints are secure and compliant with regulations and standards.
Control and visibility over endpoints
Since endpoint management provides a central platform for managing and monitoring endpoints, IT teams can easily track device inventory, enforce security policies, and troubleshoot issues, reducing the risk of unauthorized access or data breaches.
Automation of routine security tasks
Endpoint management also enables IT teams to automate routine tasks, such as software updates and security patches, which helps reduce manual effort and improve the efficiency of IT operations.
Streamlining and centralizing IT operations
Since Endpoint management provides a single console for managing and monitoring all endpoints, IT teams can simplify the management of the organization's infrastructure, enabling them to focus on higher-value activities that drive business growth.
Protection against attacks and data breaches
Endpoint Management enforces security policies and ensures that all endpoints are up to date with the latest patches and software updates. This helps reduce the organization's attack surface and minimize the risk of a security incident.
Part 9. Conclusion
Endpoints consistently expose enterprises to cybersecurity threats that malicious hackers may exploit. A versatile endpoint management solution like AirDroid Business ensures that all endpoints connecting to your network are secure and monitored for any malicious activity, and proper prevention and remediation strategies are put in place for maximum security.
Leave a Reply.